How To Change Primary Education On Handshake
How to extract all handshakes from a capture file with several handshakes
A single network information capture file (pcap format) can contain more one handshake. This can happen, for example, with the continued Airodump-ng capturing, as a consequence information technology can got several handshakes from one or more access points. Handshakes from files captured in 'noisy' atmospheric condition need additional verification and cleaning.
Several handshakes in 1 file can be obtained artificially, merely by combining them into one file. For instance, the Besside-ng program (automatically captures handshakes from all access points within reach, for this purpose conducts deauthentication attack) creates a single .cap file for all captured handshake packets.
Therefore, this is non a rare situation, and to perform an assault on the wireless networks, whose handshakes are in the same file, y'all may need to extract each handshake.
How to split handshakes on dissimilar files
Information technology is important to sympathize the divergence between a file in which several handshakes are simply merged and a capture file in a noisy environs. An example of analyzing a file of the first blazon (using aircrack-ng):
aircrack-ng FILE_NAME.cap

File example of the second type:
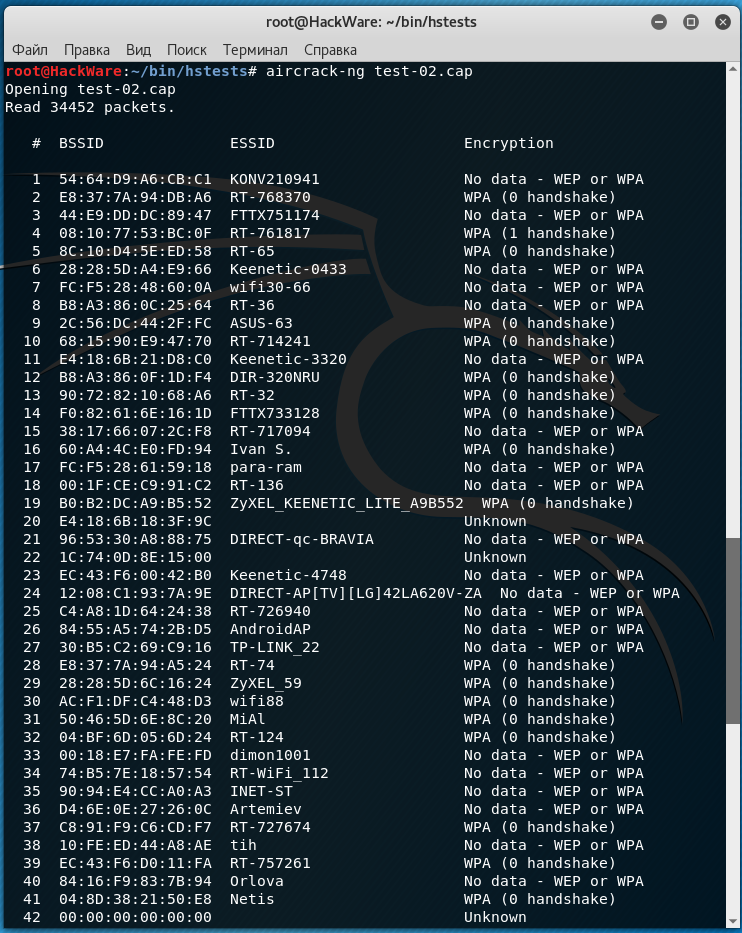
It can be seen that there is a lot of garbage in the second file, and in the whole file at that place are only 2 handshakes suitable for hacking. Amidst the garbage, there are many separate EAPOL frames (components of a handshake) that are unsuitable for countersign keen.
To view the contents of a file, yous can use Wireshark. Afterwards opening the file, use the filter:
eapol
Transmission separation handshake files using Wireshark
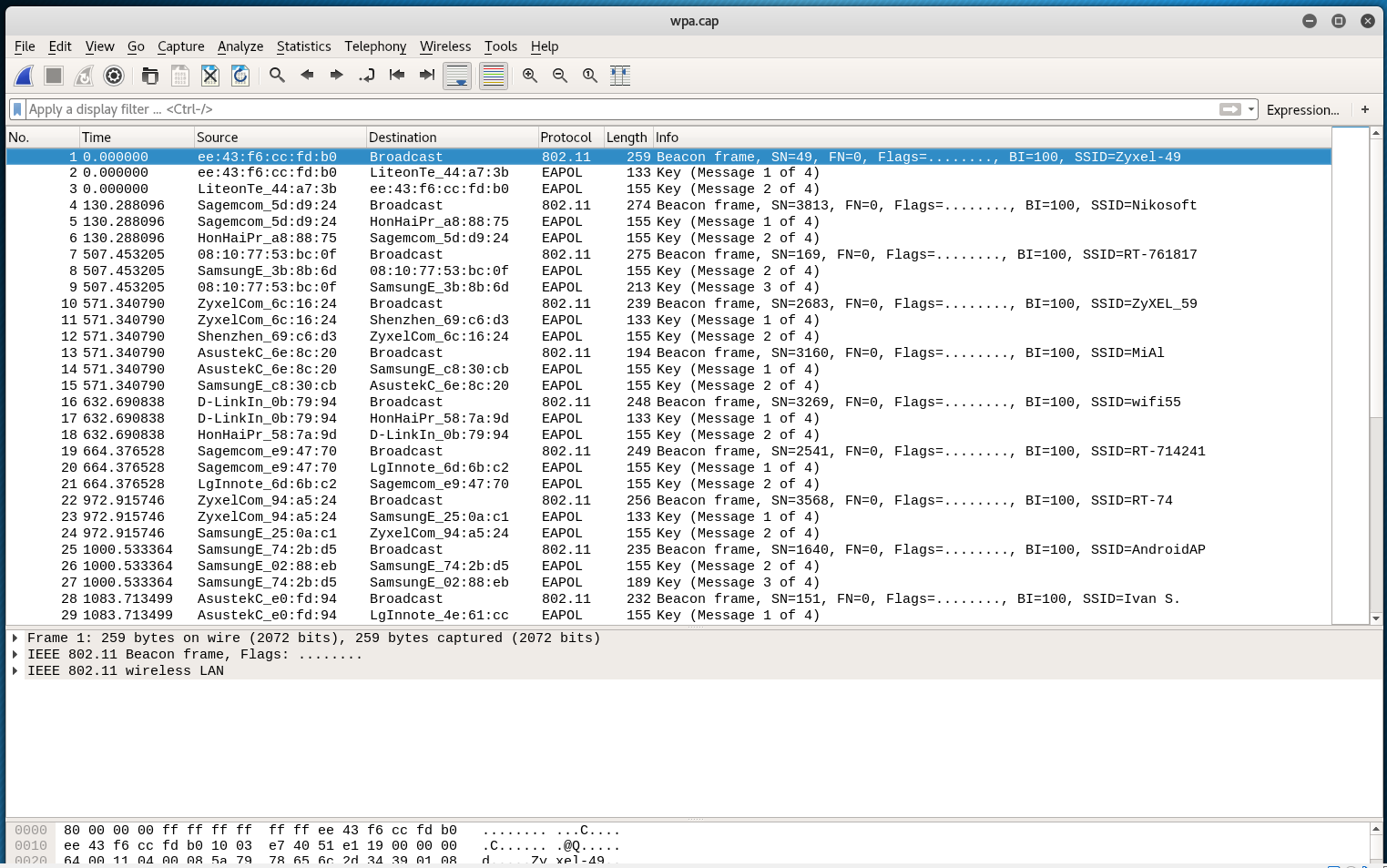
If y'all work with a file from merged handshakes, then there should not be any problems with it. Open the file in Wireshark:
Y'all tin can employ a filter
wlan.fc.type_subtype == 0x08 || wlan.fc.type_subtype == 0x05 || eapol
Only it may not be necessary, considering there are already only the necessary packages.
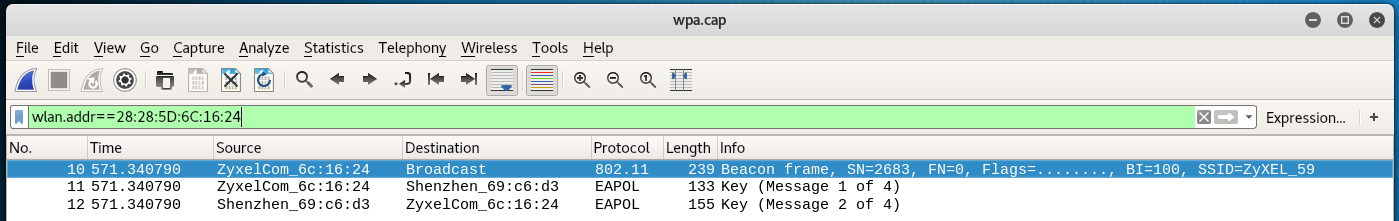
To filter packets for a specific access point, specify the BSSID with the following filter:
wlan.addr==BSSID
For case:
wlan.addr==28:28:5D:6C:xvi:24
Or and so:
wlan.fc.type_subtype == 0x08 || wlan.fc.type_subtype == 0x05 || eapol && wlan.addr==28:28:5D:6C:16:24
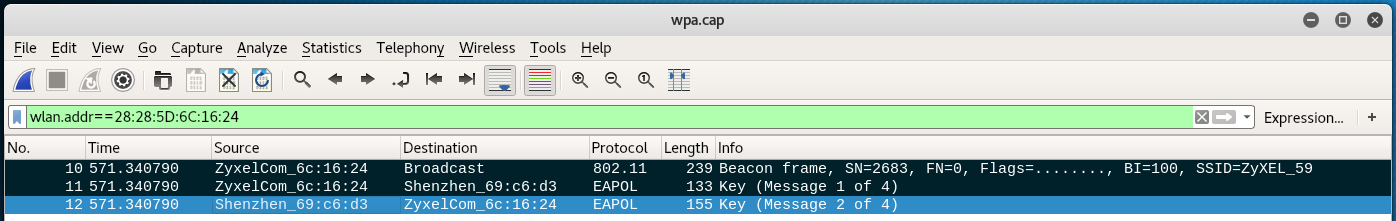
At present use CTRL+chiliad to select the required packages:
And from the File card, choose Export Specified Packets:
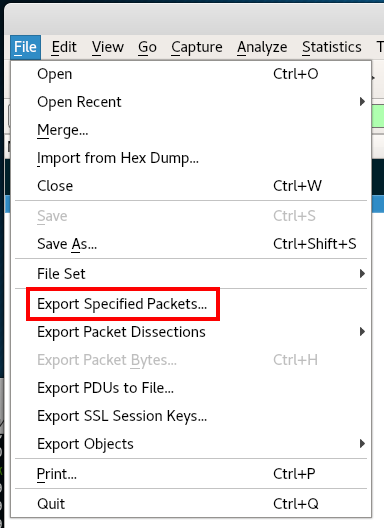
Enter the file name and put the switch on the Marked packets only:
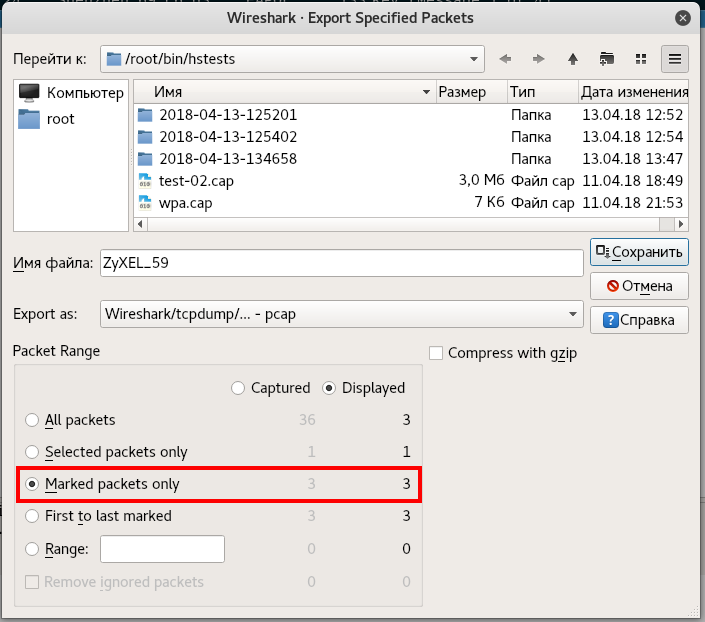
Checking our file:
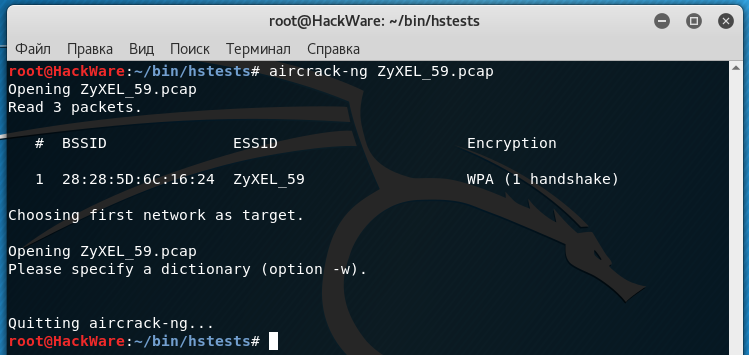
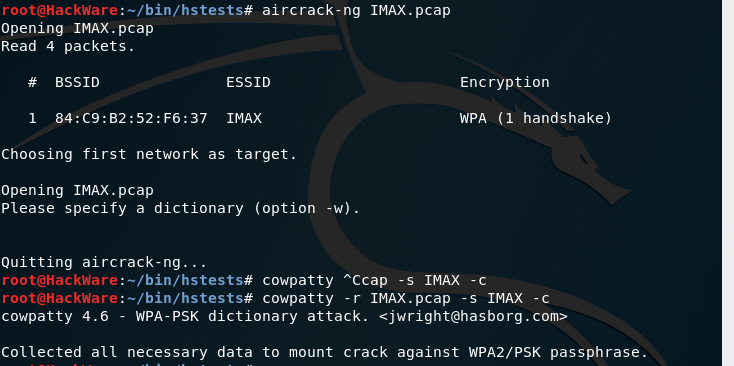
All perfectly. You can make some other check with coWPAtty past running a command similar this:
cowpatty -r FILE -s ESSID -c
For instance, in my case:
cowpatty -r ZyXEL_59.pcap -s ZyXEL_59 –c
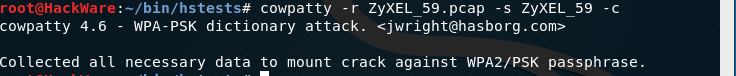
The phrase 'Collected all necessary information to mount the crack confronting WPA2/PSK passphrase' means that all the necessary information is nerveless to crack the password.
To isolate the handshake from a capture file made in noisy conditions, it is necessary to exert some effort. Start with filtering (replace 84:C9:B2:52:F6:37 with the BSSID of the network you are interested in):
wlan.fc.type_subtype == 0x08 || wlan.fc.type_subtype == 0x05 || eapol && wlan.addr==84:C9:B2:52:F6:37
The handshake is suitable for hacking the countersign if:
- necessarily includes the 2nd bulletin (M2), as well as the third ane (M3) (ensures that the connexion to the network was made) or instead of the third message contains the first message (M1) (the handshake is suitable for hacking the password, only at that place are no guarantees that connection was established and fifty-fifty that the correct countersign was entered). It is better if y'all captured all 4 messages;
- the elements of the handshake must follow in the right order;
- between them in that location should not be too much time interval (measured in milliseconds and microseconds).
We are looking at the post-obit instance.
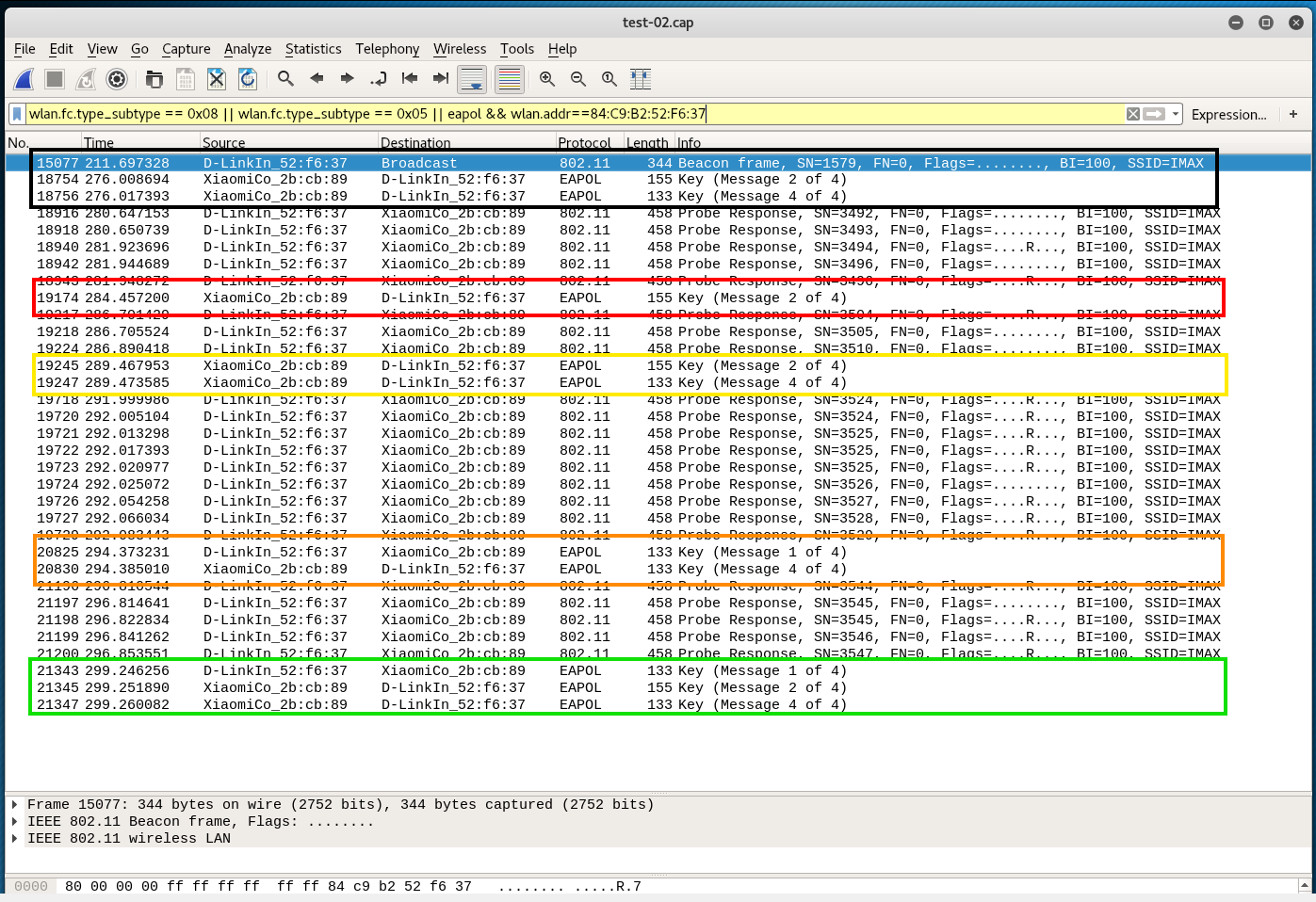
The first set of EAPOL frames (highlighted in black) does not stand for to the status that there should exist a third or beginning message in add-on to the second one.
The 2nd prepare (red): but one bulletin.
The third set (yellow): there is no tertiary or first message.
The fourth set (orangish): there is no 2nd message.
The fifth set (dark-green) is suitable, because at that place is a second and the beginning message. The time between messages seems acceptable.
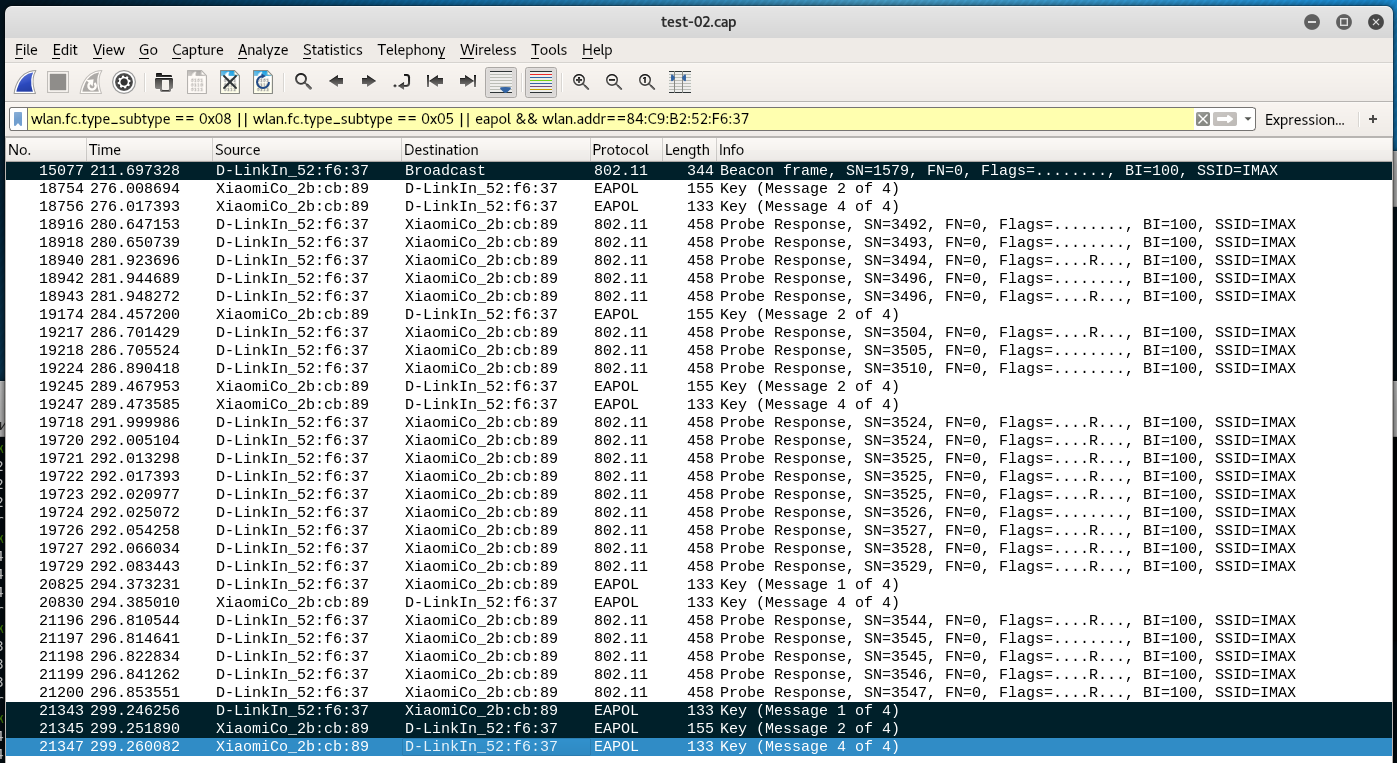
Select and salvage the necessary frames (I also include a Beacon frame):
Our file is existence tested:
Extracting a handshake with tshark
tshark is Wireshark, but without a graphical interface. This program can also exist used to carve up a big capture file into separate handshakes. To do this, the command is run as follows:
tshark -r SOURCE_FILE.cap -R "(wlan.fc.type_subtype == 0x08 || wlan.fc.type_subtype == 0x05 || eapol) && wlan.addr == BSSID" -2 -w RESULT_FILE.cap -F pcap
In information technology, you need to insert your values for:
- SOURCE_FILE.cap – file with several handshakes
- BSSID – MAC address of the access signal of interest
- RESULT_FILE.cap – file where the selected handshake volition be saved
An example of a existent command:
tshark -r wpa.cap -R "(wlan.fc.type_subtype == 0x08 || wlan.fc.type_subtype == 0x05 || eapol) && wlan.addr == 84:C9:B2:0B:79:94" -2 -w $ESSID.cap -F pcap -westward wifi55.cap
Solution of the error Unsupported file format (not a pcap or IVs file). Read 0 packets. No networks found, exiting.
Some users have an mistake when using tshark, and then opening the resulting file to aircrack-ng:
aircrack-ng MiAl.cap Opening MiAl.cap Unsupported file format (non a pcap or IVs file). Read 0 packets. No networks establish, exiting. Quitting aircrack-ng...
To avoid this error, while saving via tshark, you need to specify the -F pcap option, which specifies the correct file format.
A script for extracting handshakes
To automate the separation of ane file into handshakes, I wrote a script. Think that if you lot split a file obtained using Besside-ng or artificially when yous merge handshakes, the script volition work fine.
If you lot separate the capture file from a capture file obtained in noisy weather condition (for example, during a long running Airodump-ng), the script volition work like this:
- if no workable handshake is constitute for an access point, so all data for it will be discarded (no output file volition be created)
- if at least one work handshake is constitute for an access point, then all EAPOL frames volition be saved in one file.
Therefore, you will need to open the output files and check if there are any unnecessary data in them.
Although aircrack-ng seems to find the right handshake correctly, but with cap2hccapx (included in hashcat-utils set, used for converting to the hash format of Hashcat), problems are noticed if the unnecessary EAPOL frames from unsuitable handshakes if they are non previously cleaned.
Create a file called handshakes_extractor.sh:
gedit handshakes_extractor.sh
And copy in that location:
#!/bin/bash # Author: MiAl # Script dwelling page: https://miloserdov.org/?p=1047 AIRCRACK_TIMEOUT=2 # given time to the aircrack-ng program to read the file. Time is specified in seconds # If you take a very large file or a very deadening organisation, increase this value DIR=`date +"%Y-%one thousand-%d-%H%Yard%S"` ISDIRCREATED=0 if [[ "$1" && -f "$1" ]]; and so FILE="$ane" else echo 'Specify a (p)cap file from which you want to extract the handshakes.'; echo 'Usage:'; echo -east "\tbash handshakes_extractor.sh wpa.cap"; go out 1 fi while read -r "line" ; exercise if [ "$(repeat "$line" | grep 'WPA' | grep -E -v '(0 handshake)' | grep -E 'WPA \(' | awk -F ' ' '{print $iii}')" ]; then if [ $ISDIRCREATED -eq 0 ]; then mkdir ./$DIR || (echo "It is not possible to create a directory for saving handshakes. Quitting." && exit ane) ISDIRCREATED=i fi ESSID="$(echo "$line" | grep 'WPA' | grep -E -5 '(0 handshake)' | grep -Due east 'WPA \(' | awk -F ' ' '{impress $3}')" BSSID="$(repeat "$line" | grep 'WPA' | grep -Due east -5 '(0 handshake)' | grep -Eastward 'WPA \(' | awk -F ' ' '{print $two}')" repeat -eastward "\033[0;32mFound a handshake for the network $ESSID ($BSSID). Saved to file $DIR/\033[1m$ESSID.pcap\e[0m" tshark -r $FILE -R "(wlan.fc.type_subtype == 0x08 || wlan.fc.type_subtype == 0x05 || eapol) && wlan.addr == $BSSID" -2 2>/dev/null tshark -r $FILE -R "(wlan.fc.type_subtype == 0x08 || wlan.fc.type_subtype == 0x05 || eapol) && wlan.addr == $BSSID" -2 -w ./$DIR/"$ESSID.pcap" -F pcap ii>/dev/null fi done < <(aircrack-ng $FILE & sleep $AIRCRACK_TIMEOUT && kill -9 aircrack-ng $(ps aux | grep 'aircrack-ng '$FILE | grep -v grep | awk '{print $ii}') 2>/dev/cypher) To start, specify the (p)cap file from which yous want to extract the handshakes.
Launch example:
fustigate handshakes_extractor.sh wpa.cap
Results:
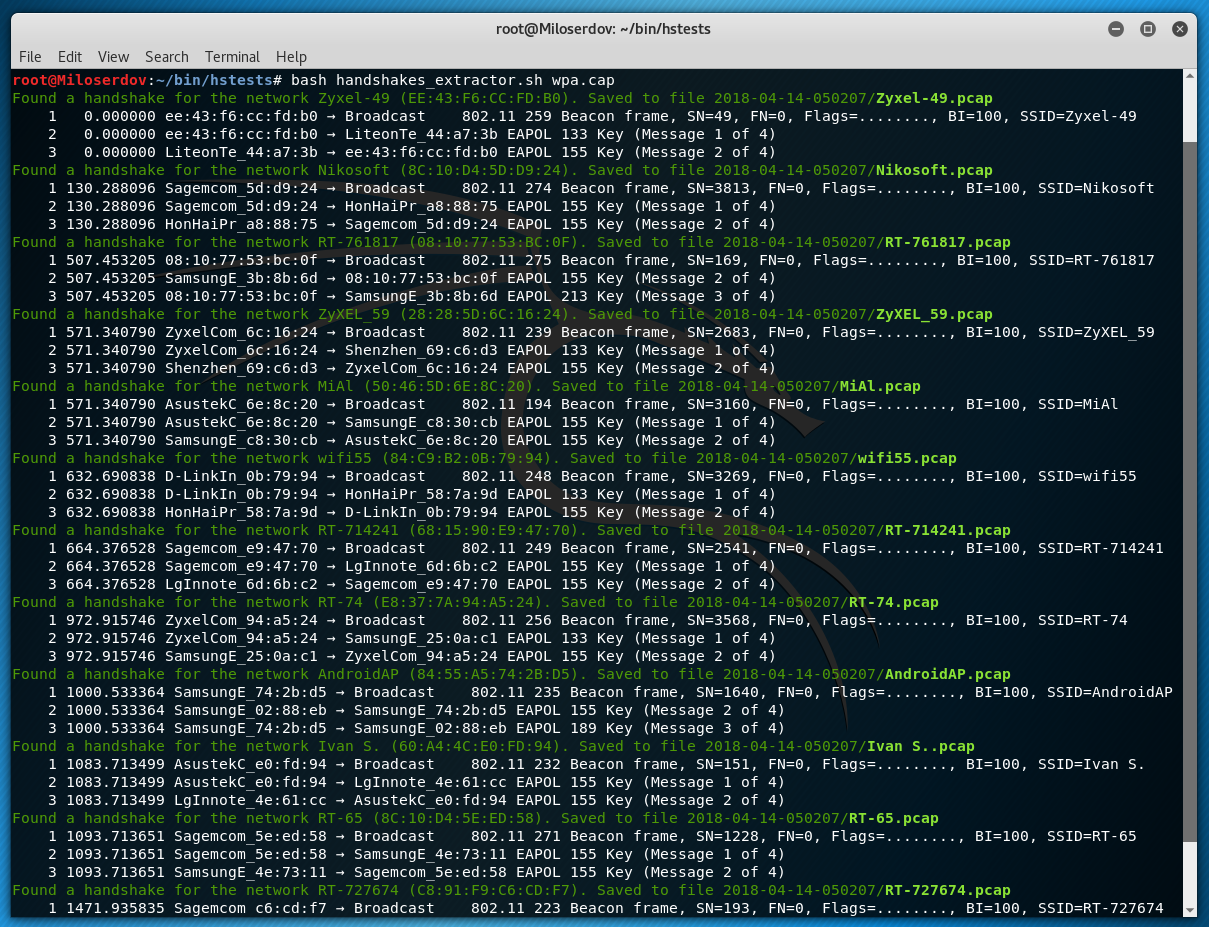
If at least one working handshake is constitute, then in the current directory a binder of the course 2018-04-13-155818 is created, in which separate handshakes for all admission points are stored as separate files.
The information virtually the file proper name with the saved frames is displayed, every bit well as information about the saved frames themselves.
When you do not demand to separate the file into split handshakes
Y'all practise not need to divide a file into separate handshakes if you are going to use the aircrack-ng programme. To select a target, yous tin use the options:
-e <essid> : target selection: network identifier -b <bssid> : target option: access signal's MAC
The cap2hccapx utility will write all the hashes (for hacking into Hashcat) into ane .hccapx file.
Run as follows:
cap2hccapx.bin SOURCE_FILE.cap. HASH_FILE.hccapx
For example:
cap2hccapx.bin wpa.cap all.hccapx

To write a hash for only one AP, specify its ESSID:
cap2hccapx.bin SOURCE_FILE.cap HASH.hccapx ESSID
Instance:
cap2hccapx.bin wpa.cap Zyxel-49.hccapx Zyxel-49
Source: https://miloserdov.org/?p=1047
Posted by: carignangatellicited99.blogspot.com


0 Response to "How To Change Primary Education On Handshake"
Post a Comment